VMware vCloud Director has several use cases. One of them is to use vCloud director for “lab management” purposes. For instance you can run several vApps simultaneous with the same IP and MAC addresses completely isolated or “fenced” We are currently building our own vApps for VMware training purposes. The ability to build one vApp for one student – add it to the catalog and then deploy it X amount of times is essential in our environment.
To understand fencing in vCloud Director you really need to understand the basic network concepts in vCloud director. vCloud director has three kind of networks
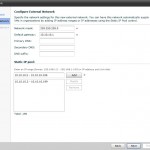
External Network: This is basically a portgroup on a standard vSwitch, Distributed vSwitch or Nexus1000. This is where you get “into” the cloud. The external network is a network where you physically have allocated a vlan and an IP segment. The IP segment can either be public internet ip addresses or private ip addresses. In our case we are using the private subnet “10.10.10.0/24” When you define your External Network you have to define this IP segment gateway and subnet mask. Besides that you define a “static IP pool”. This pool is addresses vCloud director can manage and use for vShield edge devices and virtual machines.
Organisation network: An organisation network is a network only available to the organisation it is deployed to. This network is automatically created in vCloud Director and you don’t need to manually create the portgroup in vSphere. The Organisation network can either be 1) direct connected to an external connected (in this case we use 10.10.10.0/24) 2) routed connected with a vShield edge device (in this case a vShield edge device will have an IP on the external network example: 10.10.10.20 and another ip address on the organisation network – for instanse 192.168.0.1) or 3) no connection to an external network.
vApp network: a vApp network available to only virtual machines in the same vApp. This network is automatically created when defining it. The vApp network can either be 1) routed connected to the organisation network or 2) no connection to organisation network.
If you need more information on vCloud network concepts check out Duncans great two series post on the matter: vcd network post 1 | vcd network post 2
Fencing in vCloud Director
Option 1:
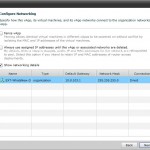
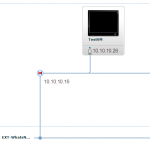
You can do fencing in vCloud director in two ways. When looking at the GUI it would seem only one. But you can actually do fencing without putting a vApp into “Fence vApp” mode. An example of this. Look at the following two screenshots. I am building a vApp that is connected to my organisation network. That means I am using my organisation IP addresses for all virtual machines in the vApp. (10.10.10.0/24). In the first screenshot I have not selected the “Fence vApp” checkmark. In the second I have selected it.
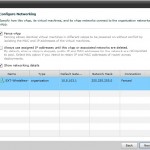
The first one is direct connected to the organisation network – and in this option I have no way of running with duplicate IP and MAC for my virtual machines. After selecting the “Fence vApp” checkmark you should notice that it changes connection type to “Fenced” and you will see NAT and FIREWALL enabled. In this case we can now copy the vApp without customization and run it serveral times with the same IP and MAC addresses.
One thing to notice about this way of doing fencing is that you can only use the “Fence” button on organisation networks. NOT on vApp networks. This will give a situation where a vShield Edge will be deployed where the internal and external interface has the same IP subnet(10.10.10.0/24), and the edge does proxy-arp and NAT
This option is probably the first one you would go to because you acutally see the “Fence” option inside vCloud Director. The truth is though, that you can do fencing without ever setting that option. And you would probably do option 2 instead.
Option 2:
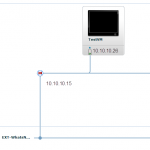
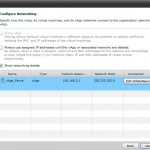
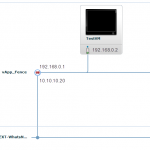
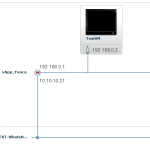
When looking at option1 we see that the vShield edge device is the one making sure we can do the fencing. In vCloud director when we create “vApp” network we can choose to make it “routed” to an organisation network. To do “manually” fencing you would create a vApp network when creating your vApp. This vApp you would connect with a routed connection to the External network. In our case we would get a “vApp” network with IP 192.168.2.0/24 with a vShield Edge Device connected and on the other side of the vShield edge you would have the 10.10.10.0/24 network.
Look at screenshot 2 and 3. This is what happens when you copy a vApp and don’t customize it. The vApp network will be the exact same. The only difference is the external IP address of the vShield Edge device. This means that you can use the external address to get “into” your vApps virtual machine with a simple NAT rule.
Summary
Fencing can be done in two ways. Both use the vShield Edge Device.
Option 1: Use the “Fence” option and use your organisation IP range directly on your fenced virtual machines. (same inside and outside IP range 10.10.10.0/24)
Option 2: Create a vApp network and make it “routed”. In this case you have one internal IP segment192.168.0.0/24 and one external IP segment 10.10.10.0/24)
Thanks for this Frank, it’s very timely for me as I’ve just started looking at vCD specifically for this fencing functionality. Do you know of any limitations? My ‘vApp’ would consist of about 80 servers , which represents a working ecosystem I’d like to replicate several times over. I need to keep the IPs the same for each deployment but keep each one largely isolated.
Hi Ed, I don’t see any problem with running a vapp with 80 servers fenced. Use the fast provisioning feature to save disk space and deploy in a few minutes.
@490c21286c1e9c7639d9d03bddb5e143:disqus Jason Boche has also a good post on this topic and Kendrick’s comment is spot on and addresses your concern…
http://www.boche.net/blog/index.php/2012/02/27/vmware-vcenter-as-a-vcloud-director-vapp/
@frankbrix:disqus Excellent post. Networks are one of the most difficult topics to understand in vCD and your post clarifies it perfectly.
Thanks Didier, it’s definitely on the right track – now I just have to work out end user access for a team of devs/users, NFS access to an ‘outside’ Netapp and how we’d manage a vCD platform. Should keep me busy for the rest of the weekend!
Hi Frank, great article which helps to understand networks in vCD. In Option 2, can you capture the vApp (and the vApp network) to a catalog? I tried this but when adding a new vApp from catalog the vApp network is not preserved….
Hi, Yes you can capture it to the catalog and deploy it with the same network preserved. When you capture the vApp to the catalog make sure that your have marked the option “When using this template” with “Make identical copy”
Sweet! Thanks.
-gogogo5
what if a server running the vshield edge device fails, all VMs on all those (potentially hundreds) of VMs on those 80 servers that relies on that single vshield edge device fails as well right ? how long would it take to bring up those hundreds of VMs? also – try to imagine the traffic flows from all VMs to their vshield edge gateway (on some free host) and then back out to thier final destination , what is your estimate QOS/SLA for all those VMs ?
Hey Frank, can fenced vApps have access to the internet ?
Yes, fenced vapps can have access to the internet. No problem.
Do you know of any limitations? My ‘vApp’ would consist of about 80 servers , which represents a working ecosystem I’d like to replicate several times over. I need to keep the IPs the same for each deployment but keep each one largely isolated.
Very curious thought
http://www.plagiarismdetect.com
Hi Susan,
There is no problem with having a vapp fenced with 80 virtual machines. You wont have any problems with that.
Frank
Hi Frank, Is it possible for you to please help post a step-by-step guide to configure option 1 – the internal and external interface has the same IP subnet(10.10.10.0/24), and the edge does proxy-arp and NAT
Hi Frank,
Just a query on this – the make identical copy option etc. is known to me and when deploying the whole vApp all works wonderfully, MAC addresses are retained etc. However, if I then create a new vApp and add VMs individually from cat vApps, then the MAC addresses are reassigned randomly again – is there a way to add individual VMs to a new vApp from a cat vApp whilst retaining the original MACs?
I have fenced network, I am able to ping any website (google.com) from vCloud VM, but unable to browse any website from browser. Am I missing any configuration?