A cool new feature on a Distributed Switch in vSphere 5.5 is the ability filter and tag traffic on a Port Group level. This capability is also referred to as access control lists (ACLs), and it is used to provide port-level security. You can create rules of the following qualifiers:
- MAC Source Address and Destination Address qualifiers
- System traffic qualifiers – vSphere vMotion, vSphere management, vSphere FT, etc.
- IP qualifiers – Protocol type, IP SA, IP DA, and port number
When a Package has been classified you can choose to either filter or tag the packets. It is very simple to implement this feature.
Step 1: Create a new vSphere 5.5 Distributed Switch or upgrade an existing. Your ESXi hosts need to be running 5.5 to be able to participate in a 5.5 dvSwitch.
Step 2: Create a port group or go to an existing.
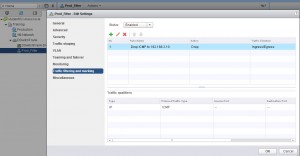
Step 3: Right click the port group and “edit settings” – then go to “Traffic filtering and marking”
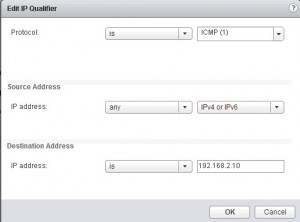
Step 4: Enable the feature. Then create what ever rule you feel like. In my environment I created a rule to drop ICMP packages with a destination of 192.168.2.10 (my DNS server).
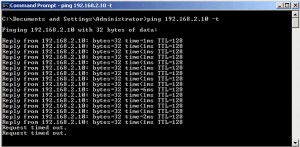
After enabling the rule my virtual machine immediately stopped getting ICMP replies.
Question:
When dropping packets, would there be an option to LOG the packets which are being dropped?
Thanks